FOR IMMEDIATE RELEASE – Tampa, FL, February 28, 2025
Wolf Bot AI, a leader in AI-powered ecosystems for digital agencies and consultants, proudly announces the launch of its newest innovation: the AI Identify Agent. This state-of-the-art tool leverages advanced machine learning algorithms, big data analytics, and real-time market insights to transform the way digital agencies approach lead generation. By automating the prospect identification process, the AI Identify Agent empowers agencies to pinpoint high-value prospects with unprecedented precision, ultimately driving higher conversion rates and fueling sustainable business growth.
In today’s competitive digital landscape, agencies are inundated with vast amounts of market data. Traditional lead generation methods, which often rely on manual research and guesswork, can be time-consuming and inefficient. Recognizing these challenges, the AI Identify Agent has been meticulously engineered to analyze diverse datasets and detect subtle patterns that indicate promising leads. By harnessing the power of advanced machine learning, the system continually refines its predictive models, ensuring that its recommendations become more accurate and effective over time.
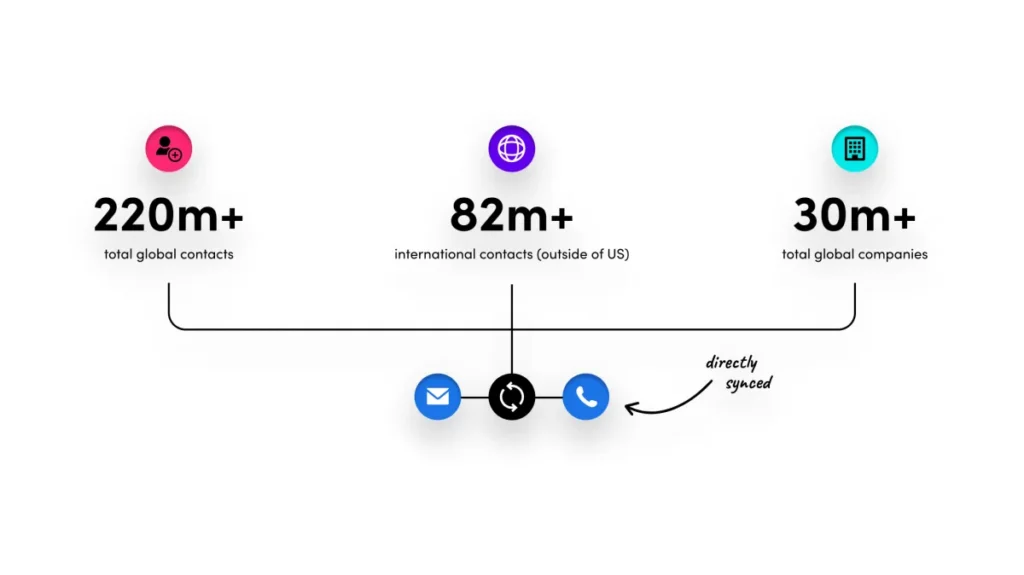
The AI Identify Agent automates the process of prospect identification, enabling agencies to effortlessly segment and target potential leads. This revolutionary tool dramatically reduces the time and resources spent on manual research, allowing agency teams to focus their energies on engaging with qualified prospects. Through seamless integration with popular CRM systems, the AI Identify Agent ensures that all leads are automatically captured, updated, and prioritized based on real-time data. This dynamic integration not only streamlines the lead management process but also helps agencies capitalize on opportunities as soon as they arise.
One of the standout features of the AI Identify Agent is its ability to deliver actionable insights in real time. As market conditions evolve, the tool provides up-to-the-minute data that allows agencies to make informed decisions quickly. These insights help in identifying market trends, emerging opportunities, and shifts in consumer behavior—information that is critical for crafting effective marketing strategies. By converting raw data into actionable intelligence, the AI Identify Agent transforms complex market information into clear, strategic directives that drive tangible results.
“Digital agencies face the daunting challenge of sifting through endless data to find leads that truly matter,” said William Schimensky, Founder at Wolf Bot AI. “Our AI Identify Agent is a game-changer because it automates the entire lead identification process, delivering precision-targeted insights that translate into measurable business growth. It’s about working smarter, not harder, and our tool enables agencies to do just that.”
Beyond its powerful data analytics capabilities, the AI Identify Agent is designed with user experience in mind. Featuring an intuitive interface and seamless navigation, the tool is accessible to teams regardless of their technical expertise. Digital agencies can easily customize parameters to suit their specific needs, ensuring that the insights generated align with their unique business goals. Whether an agency specializes in B2B services, consumer marketing, or niche markets, the AI Identify Agent is versatile enough to deliver tailored insights that drive success.
The integration capabilities of the AI Identify Agent further enhance its value. By connecting effortlessly with existing CRM systems and marketing platforms, the tool provides a unified view of the lead generation process. This holistic approach allows agencies to track each lead’s journey from initial identification to final conversion. Moreover, the system’s scalability ensures that it can adapt to the growth and evolving demands of any agency, from small boutique firms to large-scale digital marketing enterprises.
The benefits of adopting the AI Identify Agent extend far beyond efficiency gains. Agencies that have implemented the tool report a significant improvement in the quality of their leads and a measurable increase in conversion rates. With a more precise approach to prospecting, agency teams can focus on nurturing relationships with high-value prospects, leading to higher client satisfaction and increased revenue. The tool’s ability to continuously learn and adapt ensures that these benefits are not just immediate but also sustainable in the long run.
In addition to its operational advantages, the AI Identify Agent offers digital agencies a competitive edge in the market. As consumer behavior becomes increasingly data-driven, the ability to harness sophisticated analytics and real-time insights is crucial for staying ahead of the curve. By leveraging this innovative technology, agencies can position themselves as leaders in digital marketing, offering clients advanced solutions that are backed by the latest in AI research and development.
The launch of the AI Identify Agent marks a significant milestone in the evolution of lead generation strategies. Wolf Bot AI continues to push the boundaries of what is possible with AI-powered tools, setting new standards for efficiency, accuracy, and innovation in the digital marketing space. This groundbreaking solution not only streamlines internal processes but also provides agencies with the strategic insights needed to navigate an ever-changing market landscape.
The AI Identify Agent is now available for digital agencies and consultants ready to revolutionize their lead generation strategy. To learn more or schedule a live demonstration, please visit https://wolfbot.ai/ai-identify-agent/ or contact Wolf Bot AI at 855-WOLF-BOT.
About Wolf Bot AI:
Wolf Bot AI is a trailblazer in developing AI-powered ecosystems for digital agencies and consultants. The company is committed to creating innovative solutions that empower businesses to optimize their marketing efforts, streamline operations, and achieve sustainable growth through the intelligent application of advanced technology.
By introducing the AI Identify Agent, Wolf Bot AI is not only addressing the immediate needs of digital agencies but also paving the way for the future of lead generation. With this tool, agencies are equipped to turn complex data challenges into opportunities for growth and success, ensuring that every lead is not just identified but transformed into a strategic asset.